Release 8.1.5
A67766-01
Library |
Product |
Contents |
Index |
| Oracle Advanced Security Administrator's Guide Release 8.1.5 A67766-01 |
|
This chapter contains information on how to configure Oracle for use with CyberSafe, as well as a brief overview of the steps to configure CyberSafe to authenticate Oracle users.
This chapter covers the following topics:
You enable CyberSafe authentication by performing the following tasks, each of which is fully described in the next few pages:
Step 1: Install the CyberSafe server
Step 2: Install the CyberSafe TrustBroker client
Step 3: Install the CyberSafe Application Security Toolkit
Step 4: Configure a service principal for an Oracle server
Step 5: Extract the service table from CyberSafe
Step 6: Install an Oracle server
Step 7: Install the Oracle Advanced Security and the CyberSafe adapter
Step 8: Configure Net8 and Oracle on your server and client
Step 9: Configure CyberSafe authentication
Step 10: Create a CyberSafe User on the authentication server
Step 11: Create an externally authenticated Oracle user on the Oracle server
Step 12: Get the initial ticket for the Kerberos/Oracle user
Step 13: Connect to an Oracle server authenticated by CyberSafe
Do this on the machine that will act as the authentication server.
|
More Information:
See the CyberSafe documentation listed in the "Related Publications" in the Preface of this guide. |
Do this on the machine that runs the Oracle server and the client.
|
More Information:
See the CyberSafe documentation listed in "Related Publications" in the Preface of this guide. |
Do this on the client and on the server.
|
More Information:
See the CyberSafe documentation listed in "Related Publications" in the Preface of this guide. |
For the Oracle server to validate the identity of clients, you need to configure a service principal for an Oracle server on the machine running the CyberSafe TrustBroker Master Server. If necessary, you must also configure a realm.
The name of the principal should have the following format:
kservice/kinstance@REALM
For example, if kservice is "oracle", and the fully-qualified name of the machine on which Oracle is running is "dbserver.someco.com", and the realm is "SOMECO.COM", the principal name would be:
oracle/dbserver.someco.com@SOMECO.COM
Run kdb5_edit as root to create the service principal.
# cd /krb5/admin # ./kdb5_edit
To add a principal called "oracle/dbserver.someco.com@SOMECO.COM" to the list of server principals known by CyberSafe, from kdb5_edit type the following:
kdb5_edit: ark oracle/dbserver.someco.com@SOMECO.COM
You need to extract a service table from CyberSafe and copy it to both the Oracle server and CyberSafe TrustBroker client machines. For example, to extract a service table for dbserver.someco.com, type the following from kdb5_edit:
kdb5_edit: xst dbserver.someco.com oracle 'oracle/dbserver.someco.com@SOMECO.COM' added to keytab 'WRFILE:dbserver.someco.com-new-srvtab' kdb5_edit: exit # /krb5/bin/klist -k -t dbserver.someco.com-new-srvtab
After the service table has been extracted, verify that the new entries are in the table in addition to the old entries. If the new entries are not in the service table, or if you need to add additional new entries, use kdb5_edit to append the additional entries.
At this point, you need to move the CyberSafe service table to the CyberSafe TrustBroker client machine. If the service table is on the same machine as the CyberSafe client, you can simply move it (using a command such as that shown below). If the service table is on a different machine from the CyberSafe TrustBroker client, you must transfer the file with a program like FTP. For example, to move it, type the following:
# mv dbserver.someco.com-new-srvtab /krb5/v5srvtab
Remember to transfer the file in binary mode when you use FTP.
Make sure that the owner of the Oracle Server executable can read the service table (in the previous example, /krb5/v5srvtab). Set the file owner to the Oracle user or make the file readable by the group to which Oracle belongs. Do not make the file readable to all users, since this would allow a security breach.
Do this on the same machine that is running the CyberSafe TrustBroker client.
You install the CyberSafe adapter--along with the Oracle Advanced Security option--during a typical installation of Oracle8i. Oracle Universal Installer guides you through the entire installation process.
You must set certain parameters in the Oracle server and client sqlnet.ora files. The next few pages explain the following tasks.
You can modify the sqlnet.ora file either by using the Net8 Assistant or by using any text editor. The following pages explain both methods. You modify the init.ora file by using a text editor.
This graphical interface tool makes it easy to set parameters in the sqlnet.ora file and other Oracle8i configuration files.
In the Net8 Assistant's left pane, click the Profile folder. Then go to the drop down list box at the top of the right pane, and select Advanced Security Option. The tabbed pages for the Oracle Advanced Security option appear.
Go to the menu bar and click File > Save Network Configuration.
Do this by setting the SQLNET.AUTHENTICATION_SERVICES parameter.
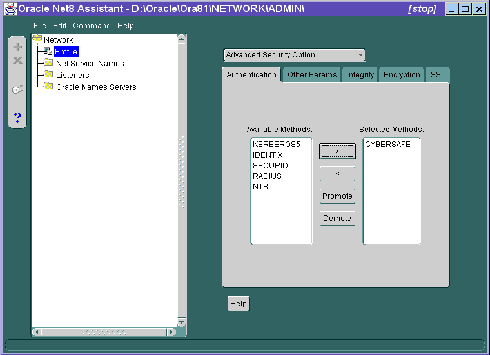
| Use the Net8 Assistant... | ...or modify SQLNET.ORA |
|---|---|
|
Refer to Figure 4-1.
|
SQLNET.AUTHENTICATION_SERVICES= |
Do this by setting the SQLNET.AUTHENTICATION_GSSAPI_ SERVICE parameter.
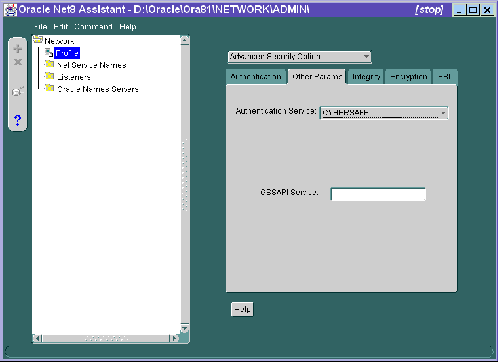
| Use the Net8 Assistant... | ...or modify SQLNET.ORA |
|---|---|
|
Refer to Figure 4-2. |
SQLNET.AUTHENTICATION_GSSAPI_ You must insert the principal name, using the format described in "Step 4: Configure a service principal for an Oracle server". |
Oracle strongly recommends that you add the following parameter to the init<sid>.ora file used for the database instance:
REMOTE_OS_AUTHENT=FALSE
where sid is the database system identifier.
Because CyberSafe user names can be long, and Oracle user names are limited to 30 characters, Oracle recommends using the following null value for the value of OS_AUTHENT_PREFIX:
OS_AUTHENT_PREFIX=""
Restart the Oracle server after modifying the configuration files, so the changes will take effect.
In order for CyberSafe to authenticate Oracle users, you must create them on the CyberSafe authentication server where the administration tools are installed. The following steps assume that the realm already exists.
|
More Information:
For information on creating the realm, see "Related Publications" in the Preface of this guide. |
Run /krb5/admin/kdb5_edit as root on the authentication server to create the new CyberSafe user, that is, "cyberuser". Type the following:
Run SQL*Plus to create the Oracle user and perform the following commands on the Oracle server machine:
SQL> CONNECT INTERNAL; SQL> CREATE USER "USNERNAME" IDENTIFIED EXTERNALLY; SQL> GRANT CREATE SESSION TO "USERNAME";
In this example, OS_AUTHENT_PREFIX is set to:
""
In the following example, OS_AUTHENT_PREFIX is set to "".
SQL> CREATE USER "JDOE" IDENTIFIED EXTERNALLY SQL> GRANT CREATE SESSION TO "JDOE"
Before users can connect to the database, they need to run kinit on the clients for an initial ticket.
% kinit (user name) Password for CYBERUSER@US.ORACLE.COM: <password not echoed to screen>
Users should run klist on the clients to list the tickets currently owned.
% klist
|
Creation Date |
Expiration Date |
Service |
|
11-Aug-95 16:29:51 |
12-Aug-95 00:29:21 |
krbtgt/SOMECO.COM@SOMECO.COM |
|
11-Aug-95 16:29:51 |
12-Aug-95 00:29:21 |
oracledbserver.someco.com@SOMECO.COM |
After running kinit to get an initial ticket, users can connect to an Oracle server without using a user name or password. Enter a command like the following:
% sqlplus /@net_service_name
where net_service_name is a Net8 service name.
For example:
% sqlplus /@npddoc_db
|
More Information:
See Chapter 1, "Introduction to Oracle Advanced Security" and Oracle8i Distributed Database Systems. |
Following are some common configuration problems and tips to help resolve them: